In traditional IT, regular security updates for computers and other devices in the network are usual. The
operating systems and anti-virus software are continuously checked for necessary updates and, if available,
updated without delay. The user oftenly doesn't notice it.
Such automatic update processes are not feasible for systems used in manufacturing and production. On the
one
hand, the most important thing is the high availability. An industrial PC that moves a tool or material
through
a machine at several meters per second cannot even stop the process for a few seconds to install software
updates. On the other hand, some software in production, such as the runtime of a SoftPLC, is only released
up
to a specified service pack. The user must then wait whether or until the manufacturer will provide an
update.
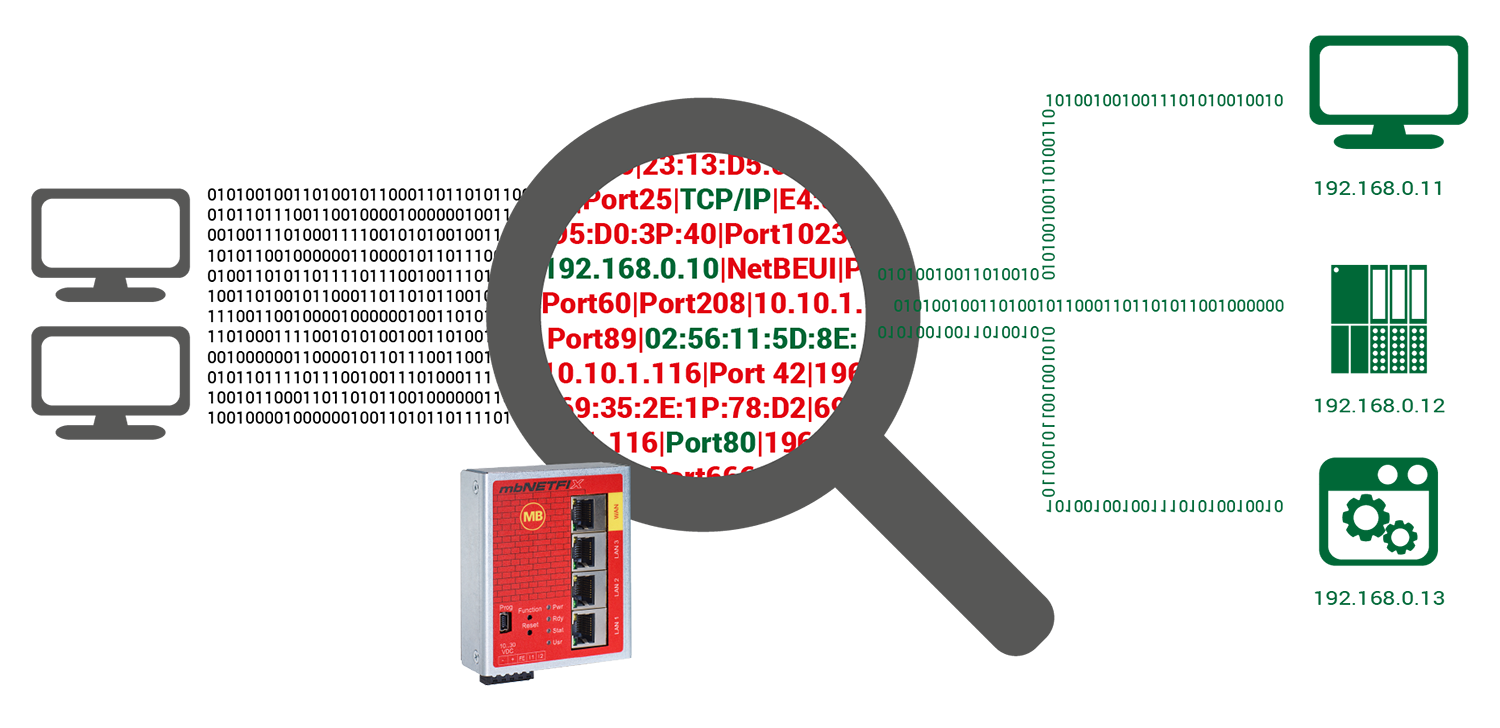
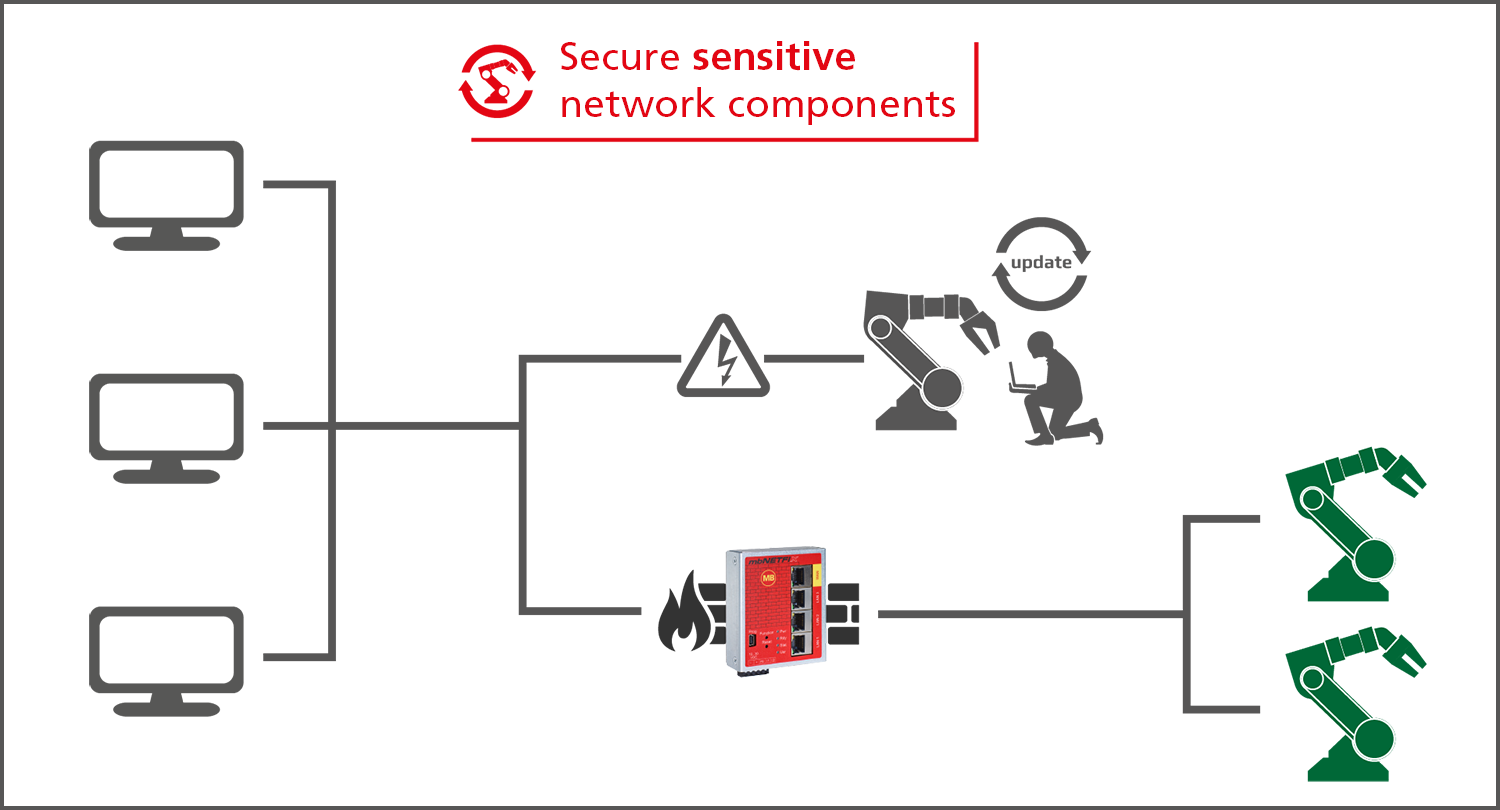
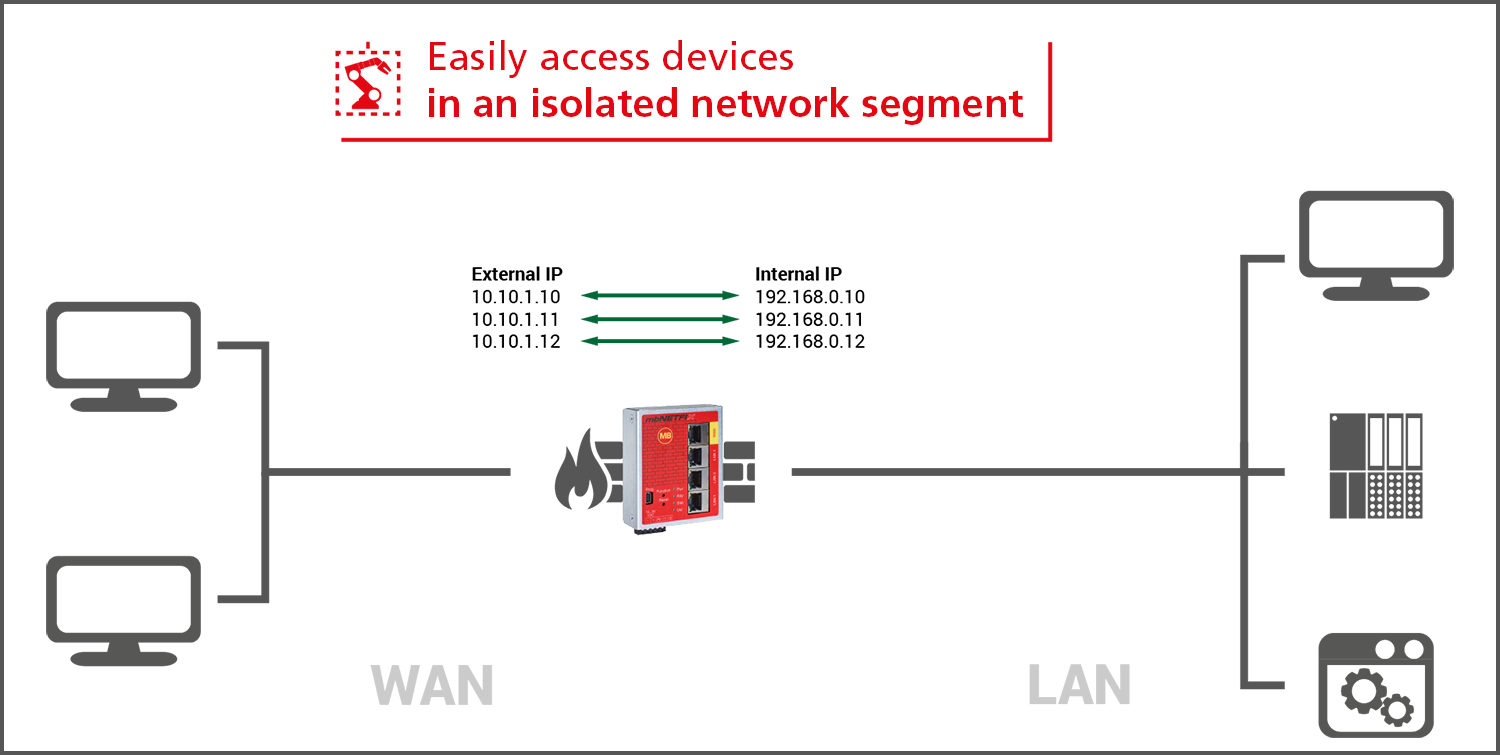
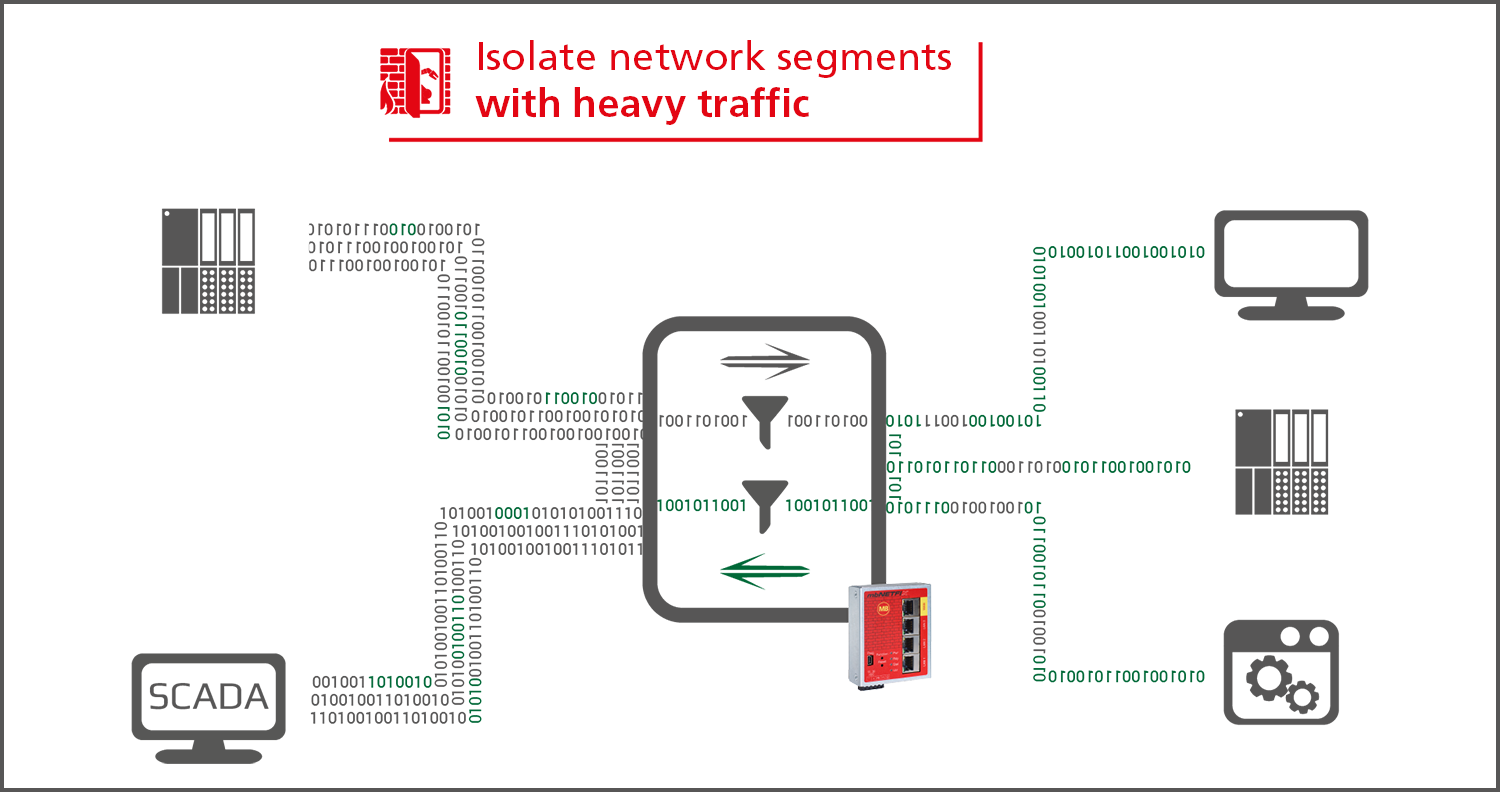
Isolating network segments
In order to achieve an effective protection against attacks from outside, the user can isolate network
segments
with the mbNETFIX industrial firewall - and only allow a defined data traffic. By creating secure zones, the
user not only defuses the update problem, but also protects device panels and controllers that do not have
any
security mechanisms of their own.
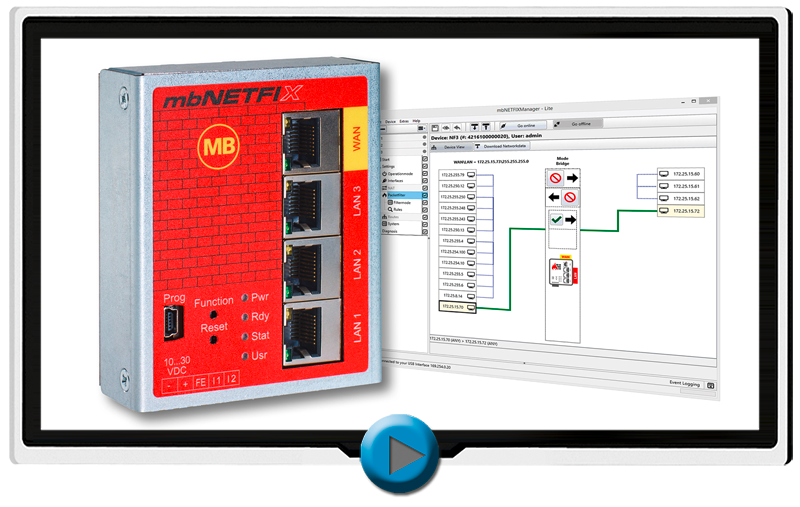
Security by design
The industrial firewall is configured simply by learning mode. Here the firewall allows unlimited
communication
and records all connections. The user then decides which connections are allowed and which are not wanted
among
the IP devices and are therefore blocked on the basis of the recorded packet table. The firewall concept is
based on "Security by Design". Even during design and development, possible threat scenarios are analyzed
and
appropriate protection is provided. In order to keep the attack vectors as small as possible, a web
interface
for configuration was deliberately omitted. Instead, the firewall is configured locally via the USB port.
For IT
experts, an SSH interface is also available, which can be optionally activated.
▪ ds
Find out more now!